SP-050-003 Data sharing
Purpose
There are many occasions when clients require us to review data for ad-hoc purposes. These cases do not fall under the typical scope of the processing that our devices carry out normally. This procedure applies specifically to such cases, particularly when clients will be sending personal data such as images.
Scope
All personal data transfers that occur are separate from the ordinary data processing activities that occur during the use of our devices.
Prerequisites
- This process ensures secure transmission of data directly to our servers located in Europe. If the data transfer must happen in a different jurisdiction, please proceed with care when following this procedure and ask the
JD-005. - This procedure assumes that there is already a contract in place between us and them. Such a contract may be a Data Processor Agreement by which we act as Data Processors of data.
- If they already are customers who have access to our device, this means that we already have the necessary contractual provisions in place and thus no other contract is necessary.
- If there is no contract in place and they are not already customers, a Data Processor Agreement must be signed in advance.
Responsibilities
JD-001 General Manager
- To approve the documents.
JD-004 Quality Manager
- To ensure that we carry out the process according to the methodology established in the present procedure.
- To check that all maintenance activities are being carried out and recording all non-conformities related that may affect the proper functioning of the processes.
JD-005 Technical Manager
- To coordinate the data transfer tasks and generate the corresponding records.
- To coordinate the correction and the documentation of any detected incidents according to the defined plan and according to the general procedure of which this specific procedure stems.
- To coordinate any questions to our Data Protection Officer.
Inputs
Regulation (EU) 2016/679 of 27 of April 2016 (GDPR)Spanish Organic Law 3/2018, of December 5 (LOPDGDD)- Data processor agreement (contract between us and the 4rd party)
GP-050 Data ProtectionISO/IEC 27001:2022
Outputs
T-050-003 Data access key
Development
Steps to follow
Create AWS path
Initially, JD-005 or a person designated by them (typically a JD-009) will create an AWS path dedicated to the specific 3rd party, utilizing that party's legal name. The client's path is established within the legit-health-clients bucket. For instance, if the 3rd party's legal name is ABC LLC, the path will be s3://legit-health-clients/ABC-LLC/images/.
Create AM user
To facilitate access to the folder, we will create an IAM (Identity and Access Management) user for them. This involves navigating to the security credentials section, selecting users, and then creating the user.
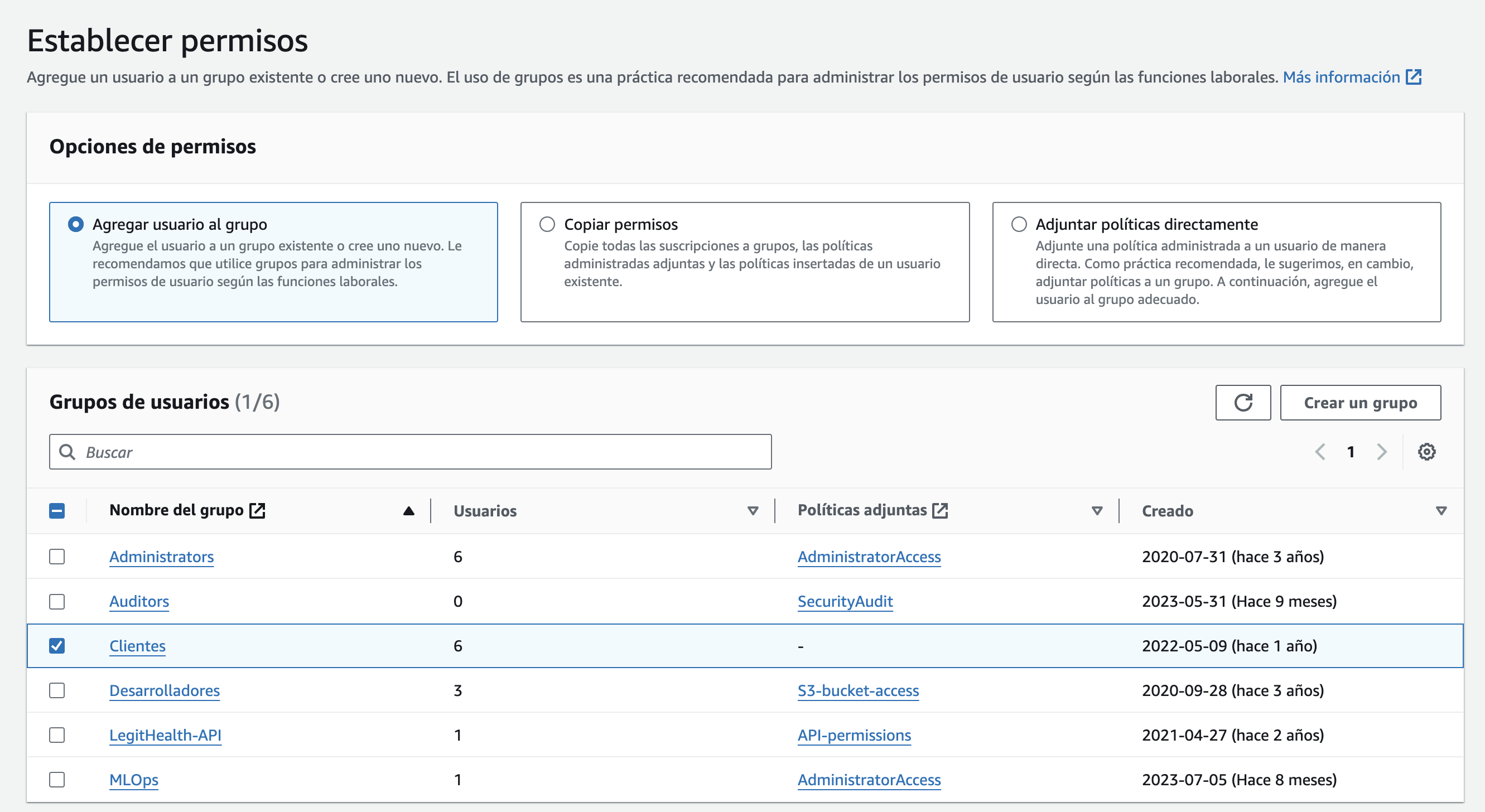
An account will be created using the company's name, such as ABC LLC, and added to the Clients group.
Next, we generate credentials for using the Amazon SDK. This includes creating an access key and opting for the CLI (Command Line Interface) option.
Subsequently, we download the CSV file containing the client's key information, which will be recorded in the T-050-003 Data access key document.
Create policy
To enable access to the designated AWS bucket path exclusively, we must create a policy for the user. The policy is created and the following JSON policy is applied, replacing ABC LLC with the actual company name:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": ["s3:ListBucket"],
"Resource": ["arn:aws:s3:::legit-health-clients"],
"Condition": {
"StringLike": {
"s3:prefix": ["ABC-LLC/*"]
}
}
},
{
"Effect": "Allow",
"Action": [
"s3:GetObject",
"s3:GetObjectAcl",
"s3:GetObjectVersion",
"s3:GetObjectVersionAcl",
"s3:PutObject",
"s3:PutObjectAcl",
"s3:PutObjectVersionAcl"
],
"Resource": ["arn:aws:s3:::legit-health-clients/ABC-LLC/*"],
"Condition": {}
}
]
}
Finally, complete the process by assigning the policy as ABC-LLC_s3_access.
Share key with the client
Once generated, create a record following the template T-050-003 Data access key and share the record with the 3rd party. This record will outline all necessary steps for them to gain access.
Finally, export the document in PDF format and secure it with a password, with the password being the first name and last name of the person who signed the contract from the 3rd party.
Signature meaning
The signatures for the approval process of this document can be found in the verified commits at the repository for the QMS. As a reference, the team members who are expected to participate in this document and their roles in the approval process, as defined in Annex I Responsibility Matrix of the GP-001, are:
- Author: Team members involved
- Reviewer: JD-003 Design & Development Manager, JD-004 Quality Manager & PRRC
- Approver: JD-001 General Manager